What is OSINT?
OSINT is gathering and analyzing publicly available data. The information can be accessed via the open internet (indexed by search engines), closed forums (not indexed by search engines) and even the deep and dark web. People tend to leave much information on the internet that is publicly available and later on results in impersonation, identity theft etc.
Techniques used for OSINT:
Using Google Dorking
Google Dorking is a technique which involves using specialist search terms and advanced search operators to find results that are not usually displayed using regular search terms. Some of the widely used Google dorks are: double quotes: Searches for the exact string. inurl: Searches for a specified text in all indexed URLs. filetype: Searches for specified file extensions. site: Searches all the indexed URLs for the specified domain. cache: Get the latest cached version by the Google search engine.
Extracting hidden directories through the Robots.txt file
The robots.txt is a publicly accessible file created by the website administrator and intended for search engines to allow or disallow indexing of the website's URLs. It is a kind of communication mechanism between websites and search engine crawlers. Since the file is publicly accessible, it doesn't mean anyone can edit or modify it. You can access robots.txt by simply appending robots.txt at the end of the website URL.
Domain owner information through WHOIS lookup
WHOIS database stores public domain information such as registrant (domain owner), administrative, billing and technical contacts in a centralized database. The database is publicly available for people to search against any domain and enables acquiring Personal Identifiable Information (PII) against a company, like an email address, mobile number etc., of technical contact. Nowadays, registrars offer Domain Privacy options that allow users to keep their WHOIS information private from the general public and only accessible to certain entities like designated registrars.
Searching data from hacked databases
Major social media and tech giants have suffered data breaches in the past. As a result, the leaked data is publicly available and most of the time contains usernames, email addresses, mobile numbers and even passwords. Users may use the same password across all the websites and that enables hackers to re-use the same password against a user on a different platform for a complete account takeover. Many web services offer to check if your email address or phone number is in a leaked database.
Acquiring sensitive information from publicly available GitHub repositories
GitHub is a renowned platform that allows developers to host their code through version control. A developer can create multiple repositories and set the privacy setting as well. A common flaw by developers is that the privacy of the repository is set as public, which means anyone can access it. These repositories contain complete source code and, most of the time, include passwords, access tokens, etc.
TryHackMe Room:
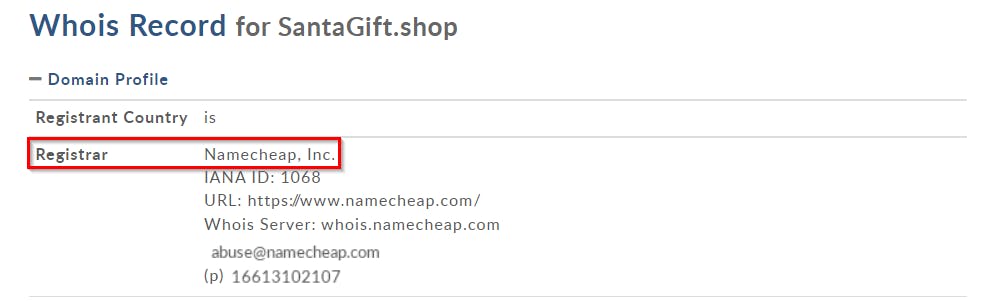
[Q1] What is the name of the Registrar for the domain santagift.shop?
[ANSWER] We will search for the information on WHOIS website.
[Q2] Find the website's source code (repository) on github and open the file containing sensitive credentials. Can you find the flag?
[ANSWER] We will search the same words that McRed searched on Github. While searching SantaGiftShop, we got this repository.
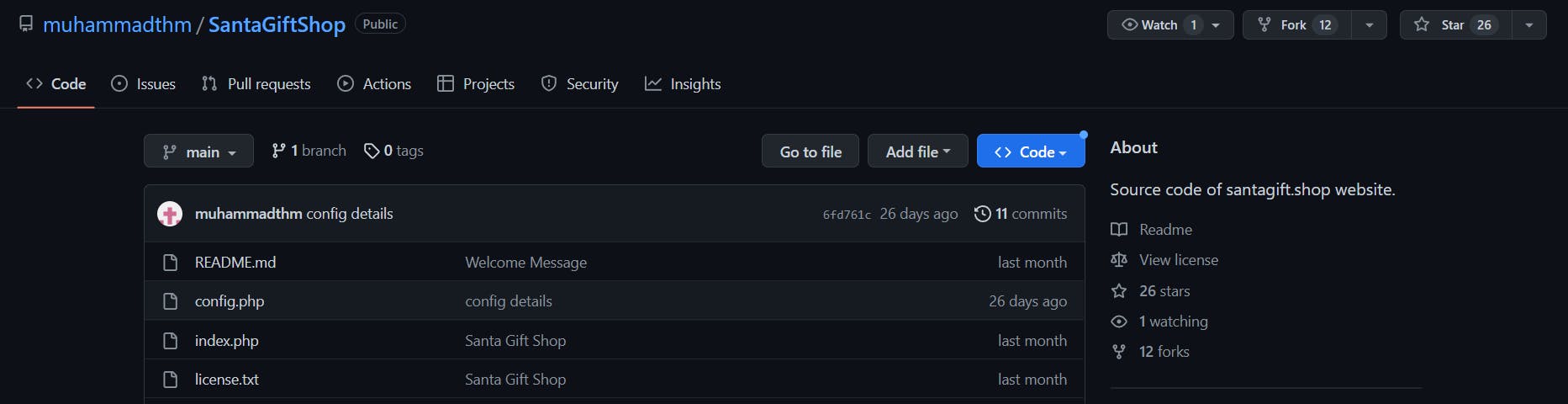 This looks as the expected repository.
This looks as the expected repository.
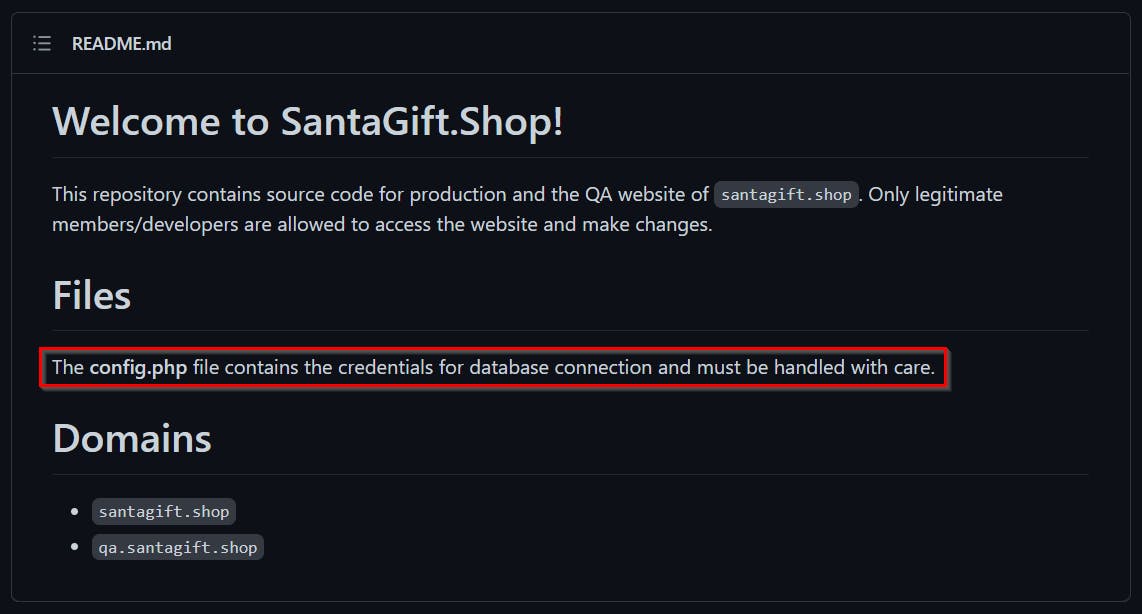 config.php is the file that contains the credentials.
config.php is the file that contains the credentials.
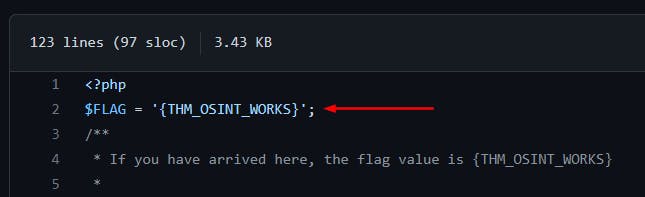 We got the flag in the config.php file.
We got the flag in the config.php file.
[Q3] What is the name of the file containing passwords?
[ANSWER] config.php as mentioned above.
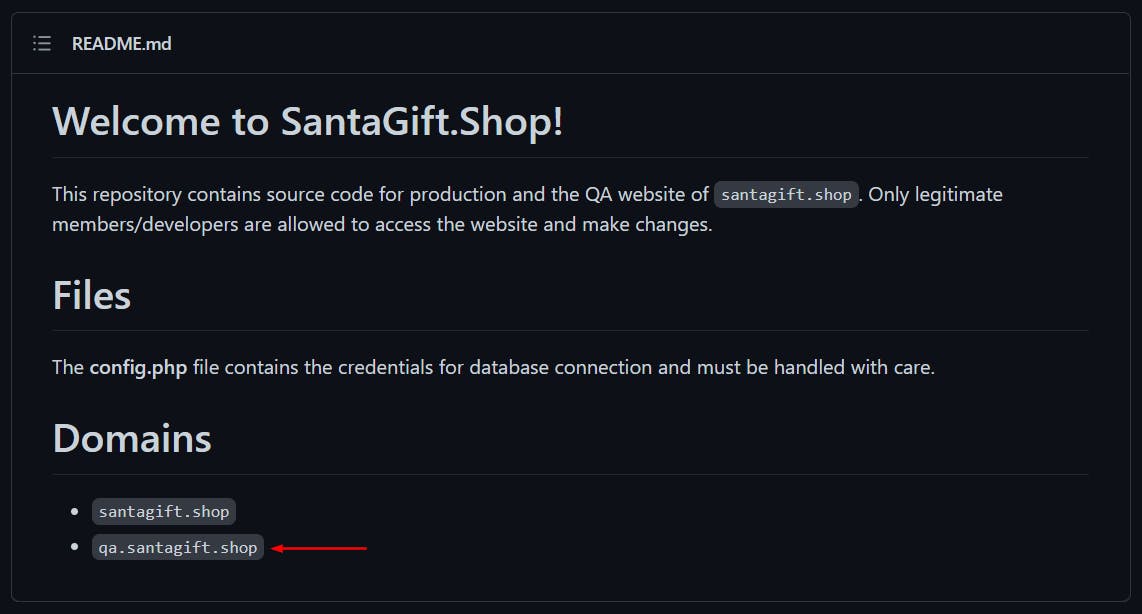
[Q4] What is the name of the QA server associated with the website?
[ANSWER] qa.santagift.shop
We got this information in the repository readme.
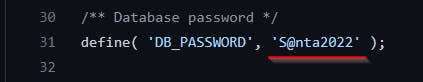
[Q5] What is the DB_PASSWORD that is being reused between the QA and PROD environments?
[ANSWER] S@anta2022
We got this information in config.php.