Remote Access Services
You can easily control your computer system using the attached keyboard and mouse when you are at your computer. How can we manage a computer system that is physically in a different place? The computer might be in a separate room, building, or country. The need for remote administration of computer systems led to the development of various software packages and protocols.
Some examples are:
SSH: SSH stands for Secure Shell. It was initially used in Unix-like systems for remote login. It provides the user with a command-line interface (CLI) that can be used to execute commands.
RDP stands for Remote Desktop Protocol; it is also known as Remote Desktop Connection (RDC) or simply Remote Desktop (RD). It provides a graphical user interface (GUI) to access an MS Windows system. When using Remote Desktop, the user can see their desktop and use the keyboard and mouse as if sitting at the computer.
VNC stands for Virtual Network Computing. It provides access to a graphical interface which allows the user to view the desktop and (optionally) control the mouse and keyboard. VNC is available for any system with a graphical interface, including MS Windows, Linux, and even macOS, Android and Raspberry Pi.
Authentication
Authentication refers to the process where a system validates your identity. The process starts with the user claiming a specific unique identity, such as claiming to be the owner of a particular username. Furthermore, the user needs to prove their identity. This process is usually achieved by one, or more, of the following:
Something you know refers, in general, to something you can memorize, such as a password or a PIN (Personal Identification Number).
Something you have refers to something you own, hardware or software, such as a security token, a mobile phone, or a key file. The security token is a physical device that displays a number that changes periodically.
Something you are refers to biometric authentication, such as when using a fingerprint reader or a retina scan.
Attacking Passwords
Passwords are the most commonly used authentication methods. Unfortunately, they are exposed to a variety of attacks.
The following are some of the ways used in attacks against passwords:
Shoulder Surfing: Looking over the victim’s shoulder might reveal the pattern they use to unlock their phone or the PIN code to use the ATM. This attack requires the least technical knowledge.
Password Guessing: Without proper cyber security awareness, some users might be inclined to use personal details, such as birth date or daughter’s name, as these are easiest to remember. Guessing the password of such users requires some knowledge of the target’s personal details.
Dictionary Attack: This approach expands on password guessing and attempts to include all valid words in a dictionary or a word list.
Brute Force Attack: This attack is the most exhaustive and time-consuming, where an attacker can try all possible character combinations.
TryHackMe Room:
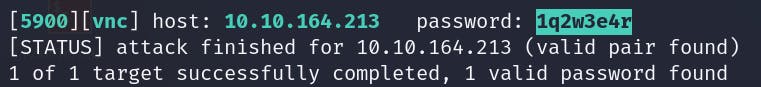
[Q1] Use Hydra to find the VNC password of the target. What is the password?
[ANSWER] We will use this cmd.

Finally, we got the password.
[Q2] Using a VNC client on the AttackBox, connect to the target. What is the flag written on the target’s screen?
[ANSWER] We will use Remmina for this task. We will login using the password that we found in the last step.

